spring'83
Spring '83 is a protocol for communication dreamed up by Robin Sloan. This project implements both a client and server for the protocol, which is based on the distribution of HTML 'boards' - limited to 2217 bytes and unable to execute JavaScript or load external resources. It also includes a key generator for users to generate their own cryptographic keys.
Description
This project implements both a client and server for the speculative protocol Spring'83, first ideated by Robin Sloan on his blog and later specified in the Spring '83 specification Draft.
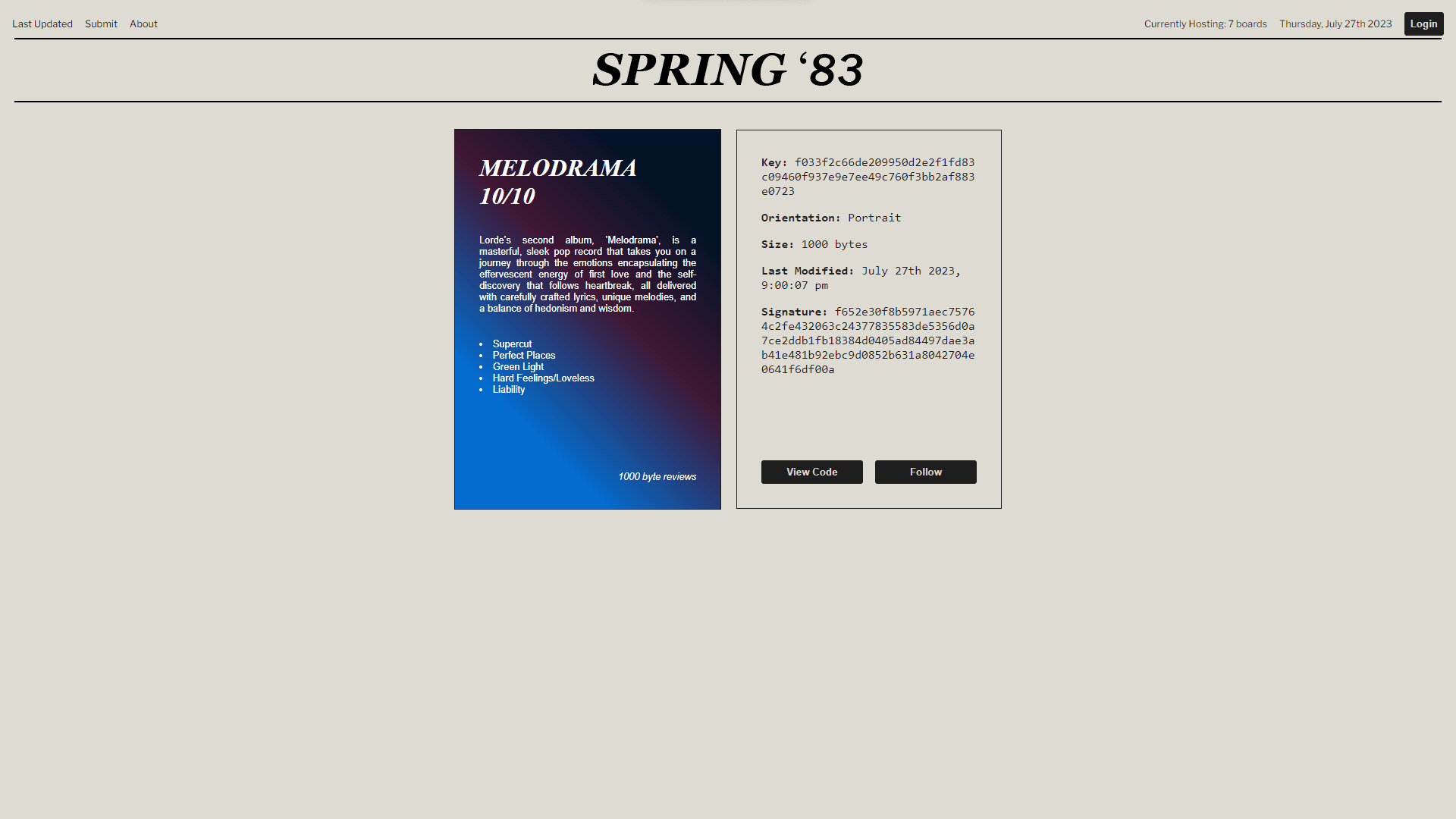
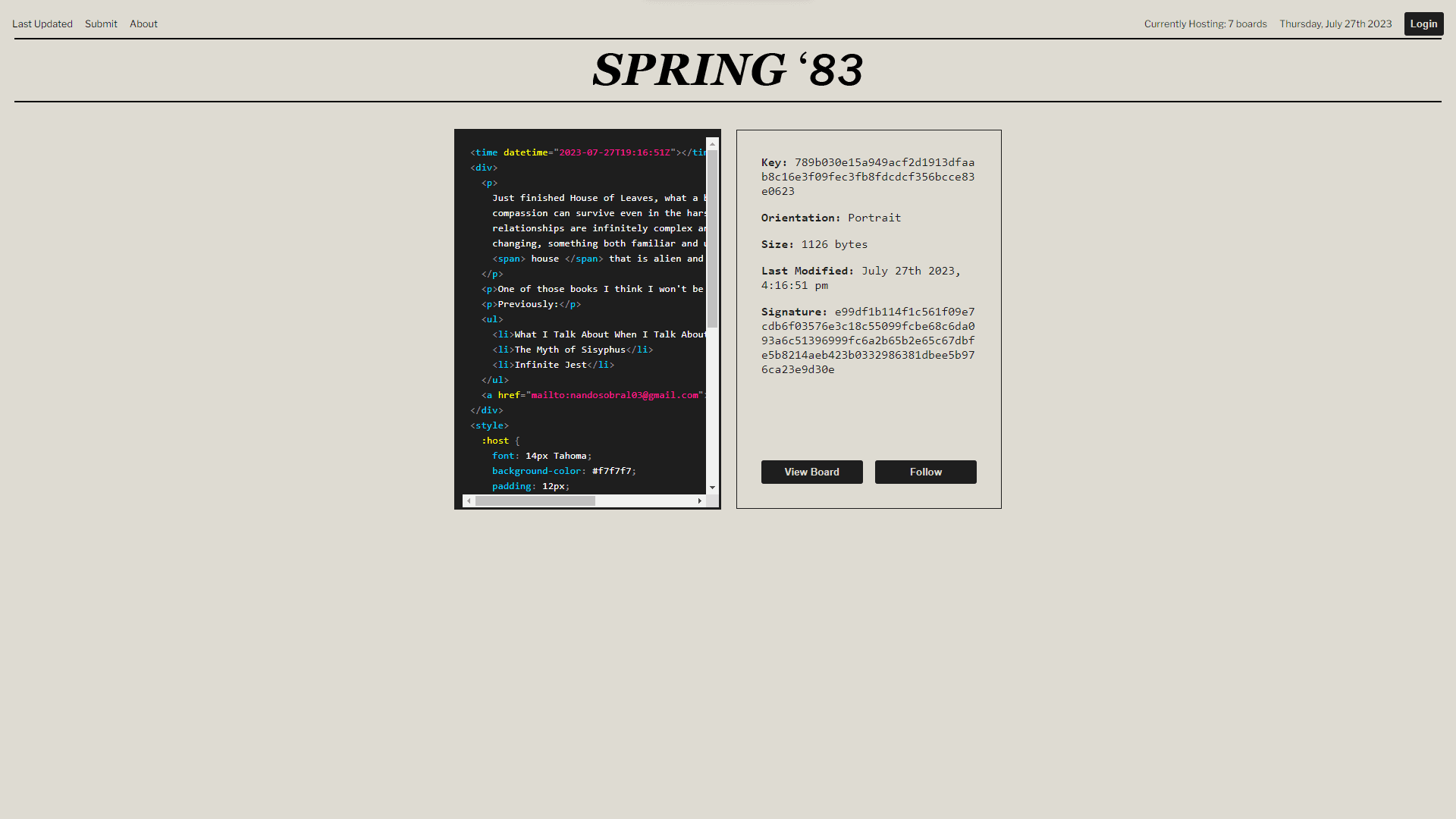
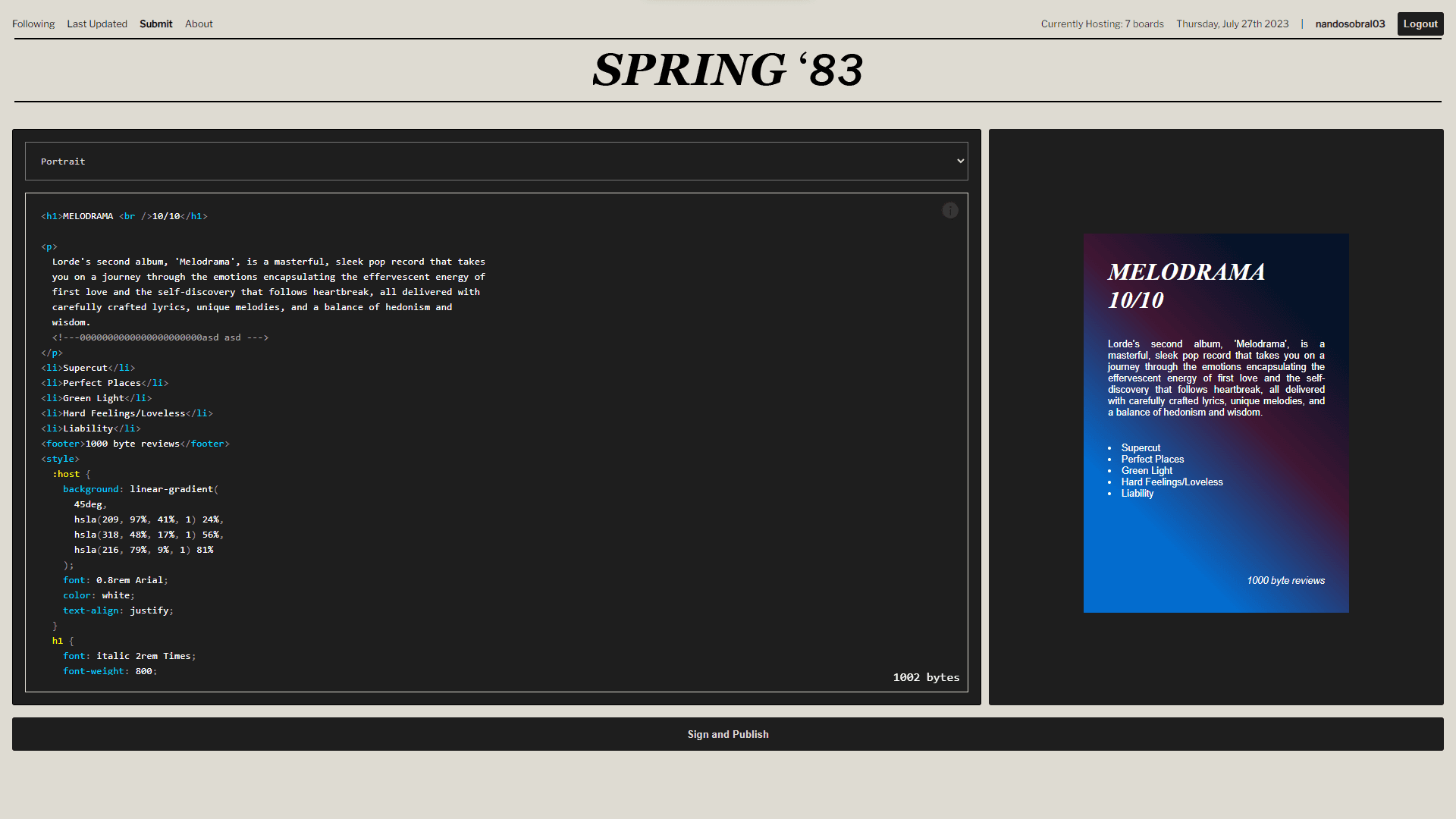
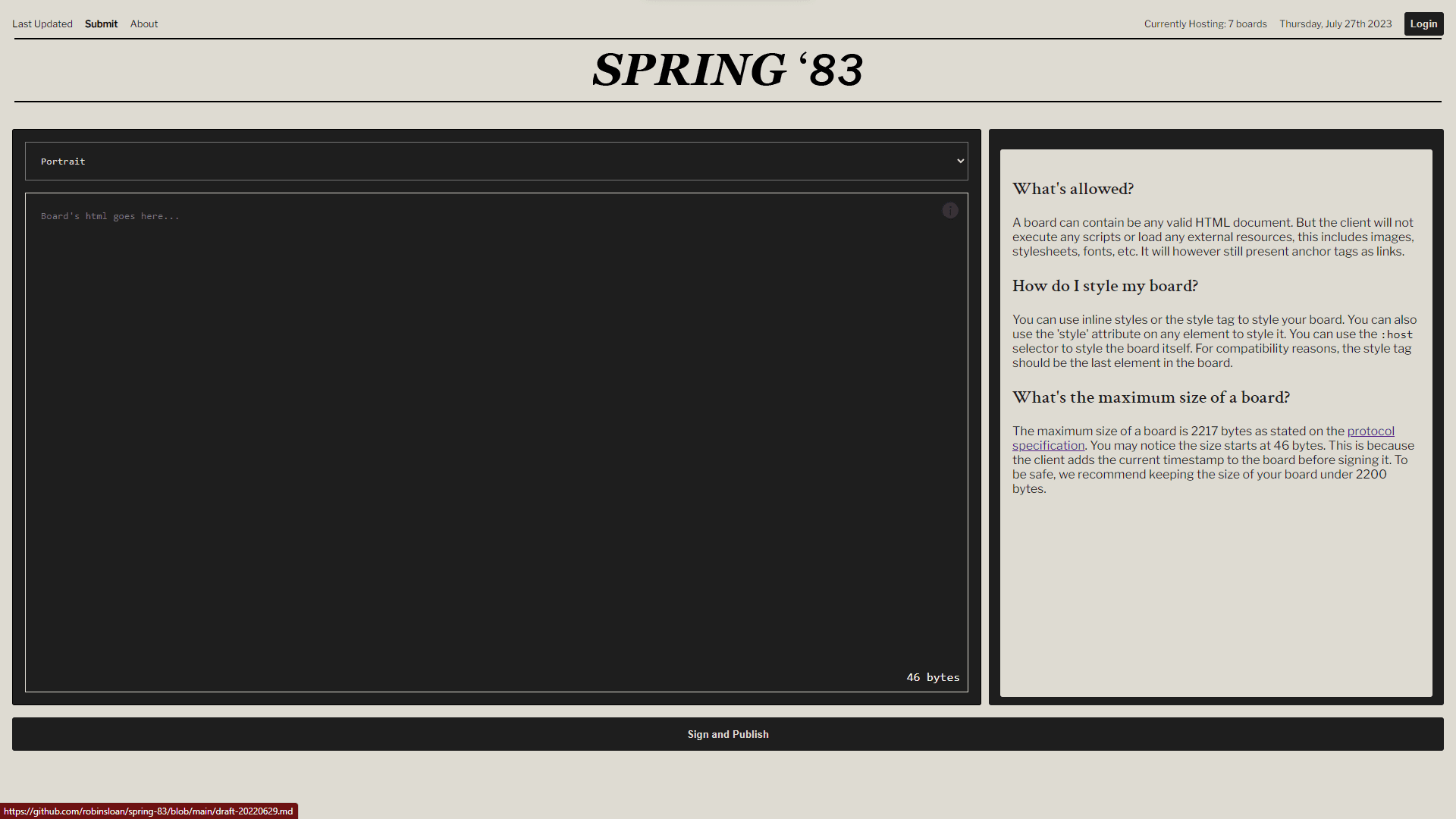
The protocol provides a simple, expressive, and predictable way to follow interesting people, regardless of their content frequency or type. Users create "boards" - HTML fragments limited to 2217 bytes, without JavaScript or external resources, but otherwise unrestricted. Publishers use public key cryptography rather than usernames, with boards being signed by their private keys. Only one post can exist per key at a time, and keys have a maximum lifespan of 2 years.
I first discovered the protocol through Honor Ash's blog and was immediately intrigued after reading the original blog post and specifications. I implemented it to learn more about the protocol while developing my backend skills with Rust.
The protocol provides a simple, expressive, and predictable way to follow interesting people, regardless of their content frequency or type. Users create "boards" - HTML fragments limited to 2217 bytes, without JavaScript or external resources, but otherwise unrestricted. Publishers use public key cryptography rather than usernames, with boards being signed by their private keys. Only one post can exist per key at a time, and keys have a maximum lifespan of 2 years.
I first discovered the protocol through Honor Ash's blog and was immediately intrigued after reading the original blog post and specifications. I implemented it to learn more about the protocol while developing my backend skills with Rust.
Technologies
The client was built using SvelteKit for its server-side rendering and routing capabilities. Authentication uses JWT tokens stored in cookies, enabling server-side page rendering with user data.
The server was built in Rust using the Axum framework, incorporating idiomatic Rust patterns for error handling and traits. MongoDB was chosen as the database for its flexibility with unstructured data.
I created two key generators: a browser-based one integrated into the client for easy access but slower generation, and a multithreaded CLI tool in Rust that generates keys 50-100x faster and allows specifying expiration years.
The server was built in Rust using the Axum framework, incorporating idiomatic Rust patterns for error handling and traits. MongoDB was chosen as the database for its flexibility with unstructured data.
I created two key generators: a browser-based one integrated into the client for easy access but slower generation, and a multithreaded CLI tool in Rust that generates keys 50-100x faster and allows specifying expiration years.
Things Learned
This project significantly improved my Rust proficiency and understanding of the Axum framework for building REST APIs with authentication. It deepened my knowledge of cryptography, particularly regarding Elliptic Curve and asymmetric cryptography.
On the frontend, I enhanced my SvelteKit skills in building responsive applications. The deployment process taught me more about Docker, particularly multi-stage builds for creating efficient container images.
On the frontend, I enhanced my SvelteKit skills in building responsive applications. The deployment process taught me more about Docker, particularly multi-stage builds for creating efficient container images.
Gallery